© 2025 Bonfy.AI. All rights reserved.
Next-Gen Data Loss Prevention for the Generative Al Age




Leveraging our multi-channel architecture and industry-leading AI driven content analysis engine, we detect and prevent exposures in AI and human-generated content in a broad set of information flows and systems, such as email, file sharing, collaboration tools, SaaS, web traffic and AI agents communication.
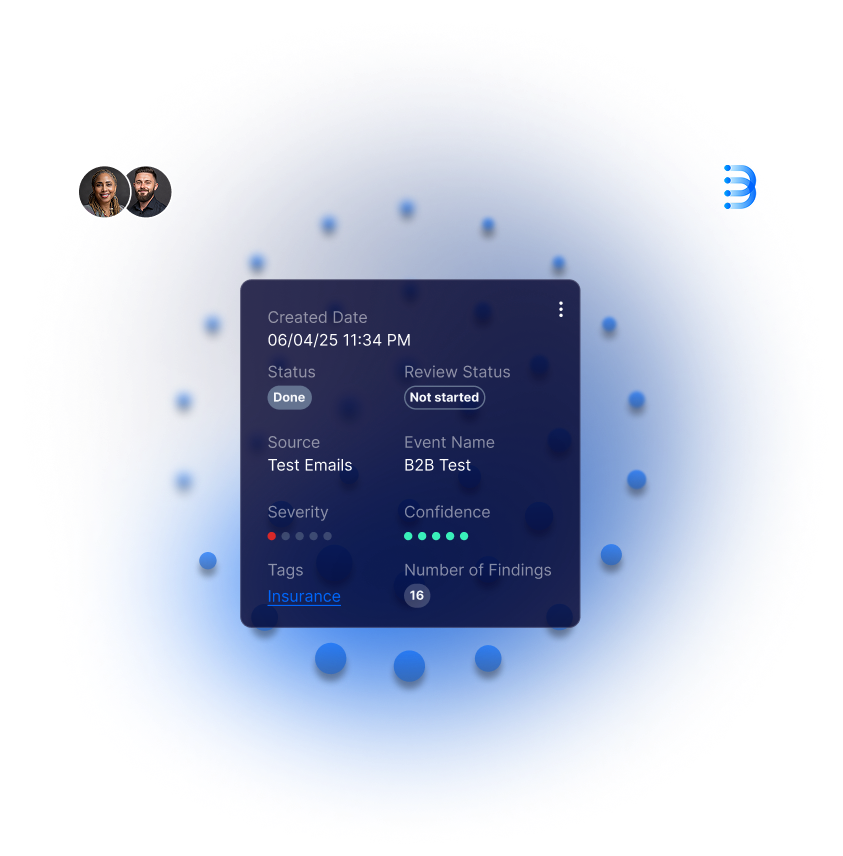
Bonfy ACS, an AI-native platform, is designed to mitigate risks of both data in motion and data at rest, enable entity risk management, and automate contextual data labeling.
We provide the only solution that uses business context and business logic for highly accurate exposure detection, reducing false-positives and associated alert noise, and increasing detection rates for the exponentially growing AI-generated content.
With comprehensive Microsoft 365 integration, we now address the growing risks associated with Microsoft 365 Copilot adoption, covering both upstream risks (sensitive information reaching LLMs) and downstream risks (confidential data being generated or distributed through Copilot interactions).
Bonfy connects to the platforms where GenAI content is created and shared, infusing them with policy logic and enterprise context. Our Adaptive Knowledge Graphs and post-generation analysis help you grasp every file, message, and Copilot output in context.
See you who authored your content, where it’s shared, and whether it violates your policies. These automated enforcement actions integrate with Slack, email, and SIEM tools to stop risks before they spread.
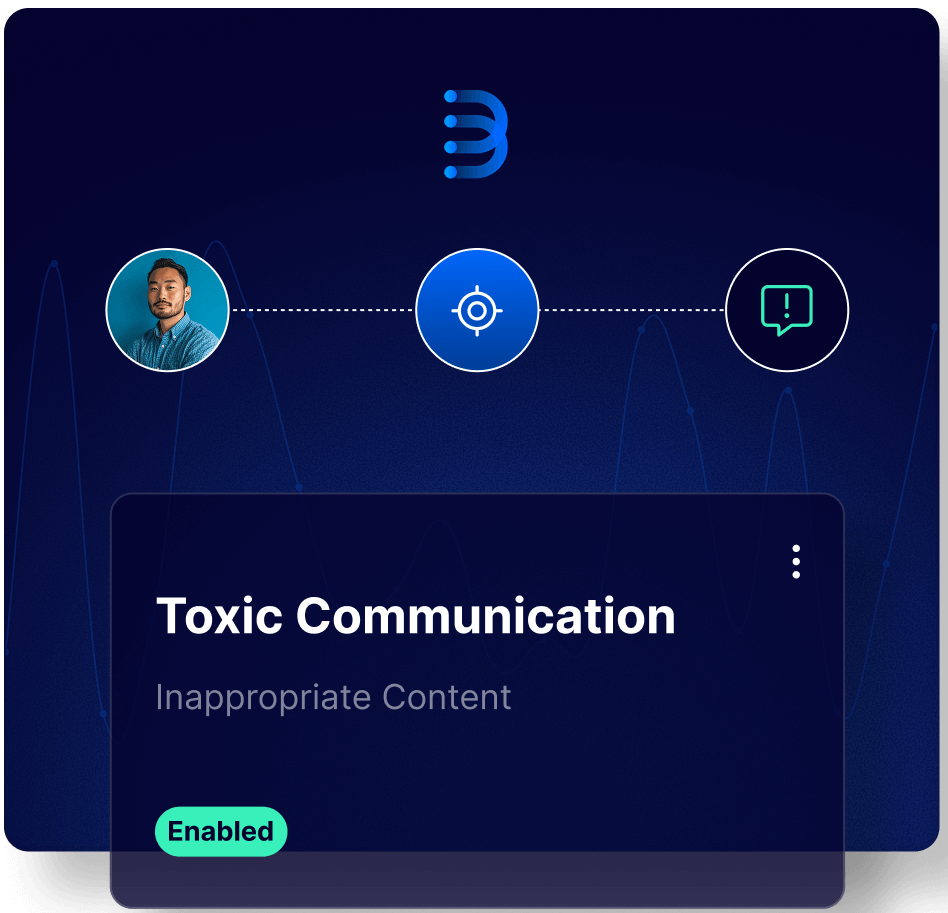







While GenAI offers transformative potential, it also brings significant risks, including breaking customer trust, information leakage, misinformation, privacy violations, copyright exposure, and harmful content. Legacy DLP solutions, reliant on outdated detection methods, struggle with false positives, missed threats, and mounting operational overhead. These challenges can result in major incidents, compliance violations, and damage to business reputation and trust.
As organizations accelerate their adoption of new AI-driven technologies to streamline productivity or to introduce automation, such as Microsoft 365 Copilot, fears around data leakage are intensifying. Modern threats require a new approach.





Overcome the limitations of traditional unstructured data security controls with adaptive, self-learning algorithms that continuously evolve to reduce false positives and negatives, speeding up investigations and improving threat detection.
With entity mapping to analyze “who” and “what” is at risk, including PII.
For deep business-context analysis.
To secure data after creation—human or AI-generated.
To reduce internal risk.
For email, chat, SaaS apps, Shadow AI tools, and custom APIs.
For instant enforcement actions.
With out-of-the-box policies (GDPR, HIPAA, PCI, CCPA, toxic content, communication safety).
Integration for real-time visibility and governance.
With BYOC, MFA, and RBAC support

From risk detection to policy enforcement, Bonfy helps enterprises stay ahead of evolving regulations and AI-driven threats by providing visibility, contextual data labeling, and implementing technical controls for data in motion and at rest. Specialized Microsoft Copilot risk management addresses both upstream and downstream AI-related risks.

Analyze communication in the form of email (including attachments), file sharing and other forms of communication prior to being sent externally, with real-time content inspection, automated risk prioritization and remediation.
Use customizable out-of-the-box policies for customer trust, privacy and IP leakage, or create your own policies.



Bonfy secures sensitive data (PII, financial info, IT secrets) with real-time risk detection, entity management, and safe AI-driven communication. Automated labeling, executive dashboards, and audit-ready reporting ensure transparency while reducing overhead.


Tech companies must protect IP, source code, secrets, and proprietary designs while enabling AI-powered development. Prebuilt policies stop leakage of critical assets like API keys, credentials, encryption keys, and code snippets.
© 2025 Bonfy.AI. All rights reserved.